Landing Zone
Overview
The Landing Zone component establishes an initial best-practice AWS multi-account setup.
Extending AWS Control Tower
Gruntwork’s suggested Landing Zone and Account Factory extends AWS Control Tower to provide additional critical functionality.
What is AWS Control Tower?
AWS Control Tower enables centralized governance and compliance for AWS accounts within an organization. However, it primarily operates as a Platform-as-a-Service (PaaS), relying on manual "ClickOps" processes for account creation and configuration. This approach contrasts with Infrastructure as Code (IaC) tools like Terraform, which emphasize codifying cloud resources. Customizing Control Tower and maintaining those customizations over time can also pose challenges.
Additional functionality
Gruntwork’s Account Factory addresses these limitations by enhancing Control Tower with the following capabilities:
- Configure and customize new AWS accounts using Terraform/OpenTofu.
- Through Gruntwork Account Factory:
- Ensure all new AWS accounts comply with the CIS AWS Foundations Benchmark out of the box.
- Request new AWS accounts using YAML files, GitHub Actions, or any system that can trigger a GitHub action (e.g. ServiceNow).
- Review and customize AWS account requests through GitHub Pull Request workflows.
- Define and apply an organization-specific account baseline.
- Automatically keep AWS account baselines up-to-date with Patcher.
Prerequisites
To use Gruntwork Account Factory, begin by setting up a new multi-account environment through AWS Control Tower. The following prerequisites must be met:
-
A new AWS account with a user granted administrator permissions.
infoThis account will serve as the root of your multi-account environment after enabling Control Tower.
-
Three unique email addresses for the logs, shared, and security (audit) accounts.
noteThese email addresses must not already be associated with an AWS root login. "+" email aliases, such as root+logs@acme.com or root+security@acme.com, are acceptable.
-
A designated home region for your Control Tower configuration.
cautionThe home region is where most workloads or data will reside. This region cannot be changed once the AWS Control Tower landing zone is set up. For guidance, refer to Administrative Tips for Landing Zone Setup.
-
A KMS Key for encrypting Control Tower resources with an appropriate permissions policy.
Step-by-Step Instructions to Create the Control Tower KMS Key
infoFor detailed assistance, refer to the AWS documentation on Guidance for KMS keys.
-
Log in as an admin user and navigate to KMS in your root AWS account.
-
Ensure you are in your home region and click Create Key.
-
Use the default parameters for key configuration.
Details
Screenshot
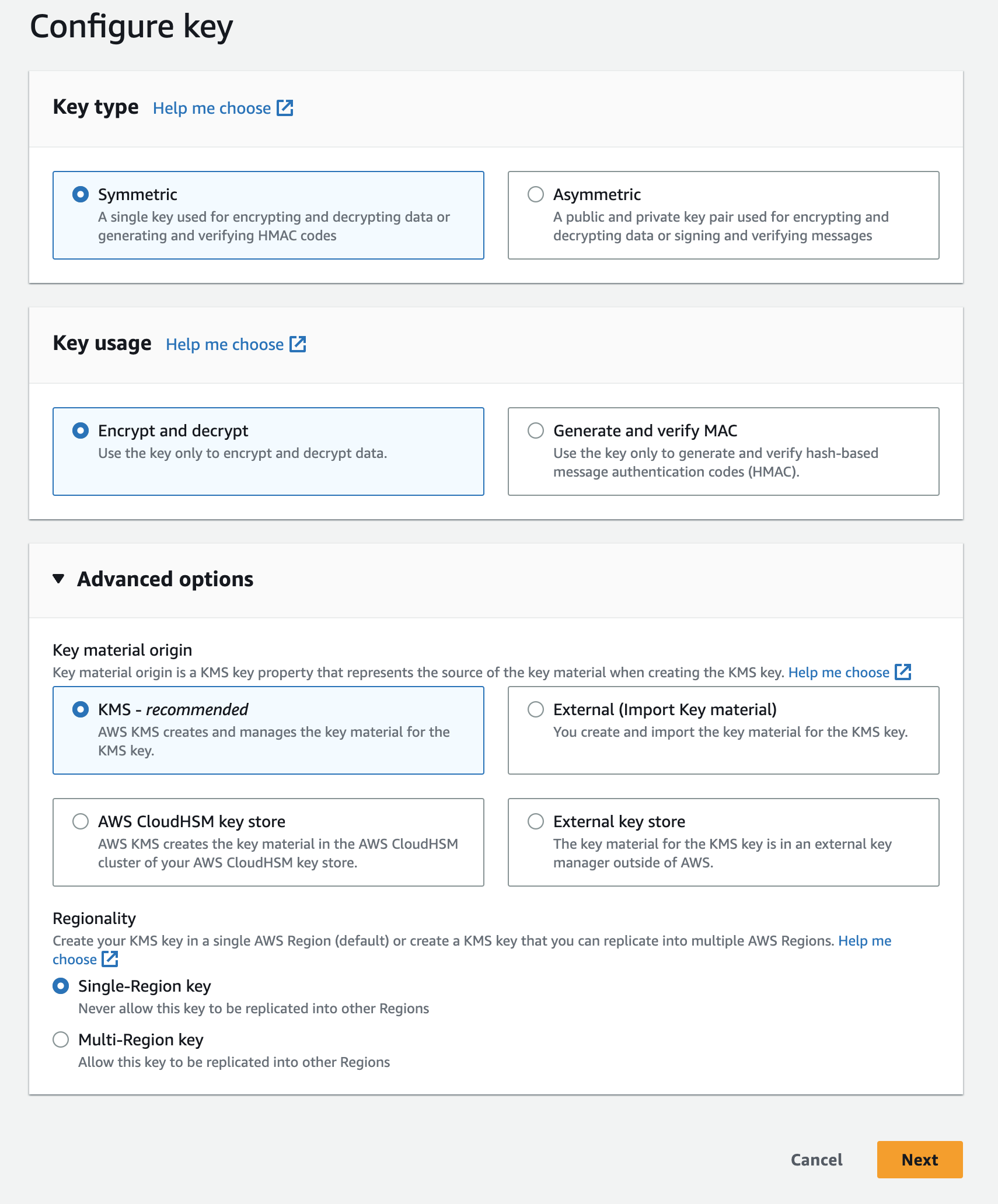
-
Assign a descriptive alias, such as
control_tower_key.Details
Screenshot
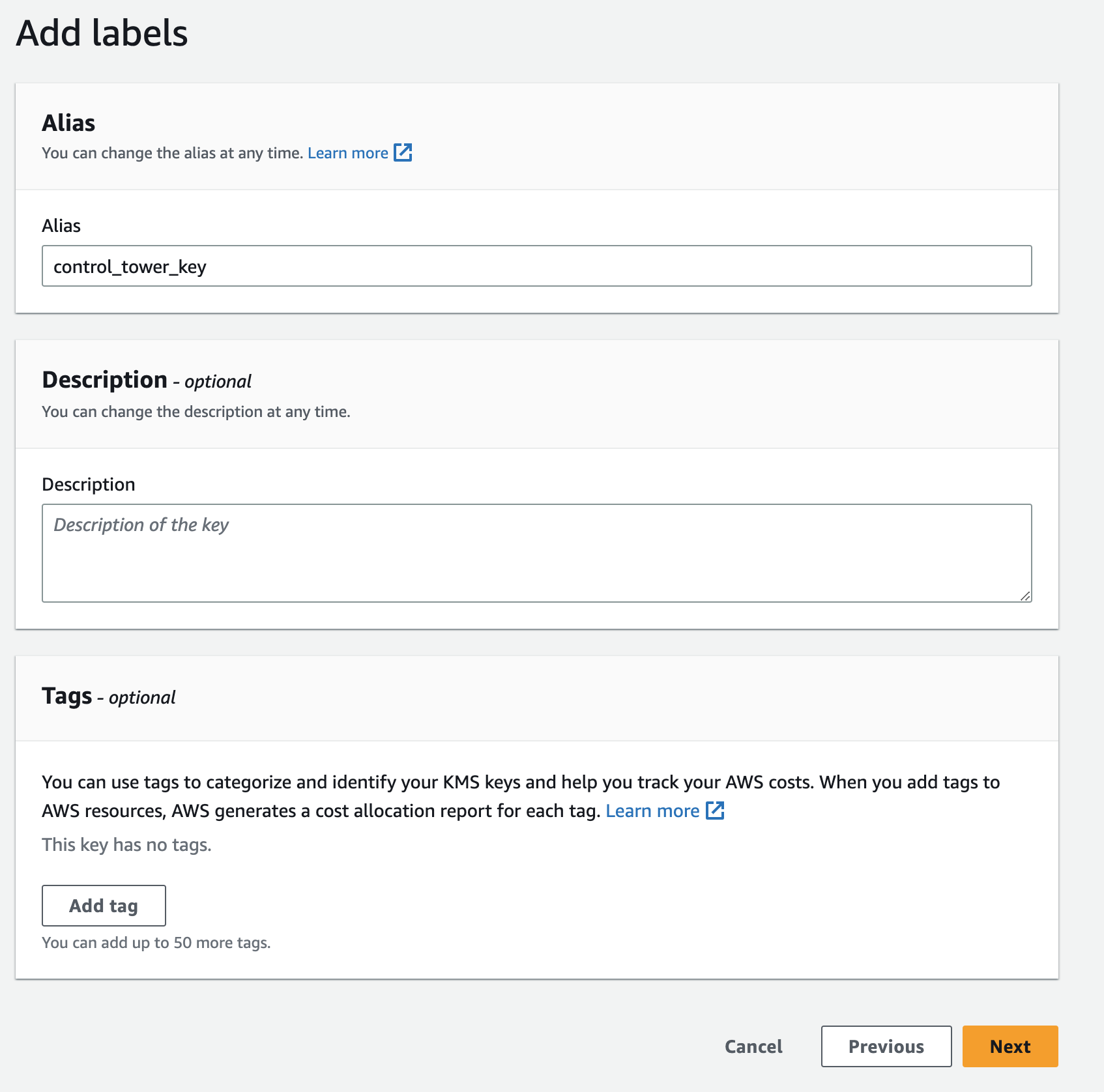
-
Designate your admin user as both a key administrator and a key user.
-
Click Finish to complete the creation of the key.
-
-
Locate the newly created key on the next screen and click to edit the following:
-
In the Key Policy tab, click Edit.
Details
Screenshot
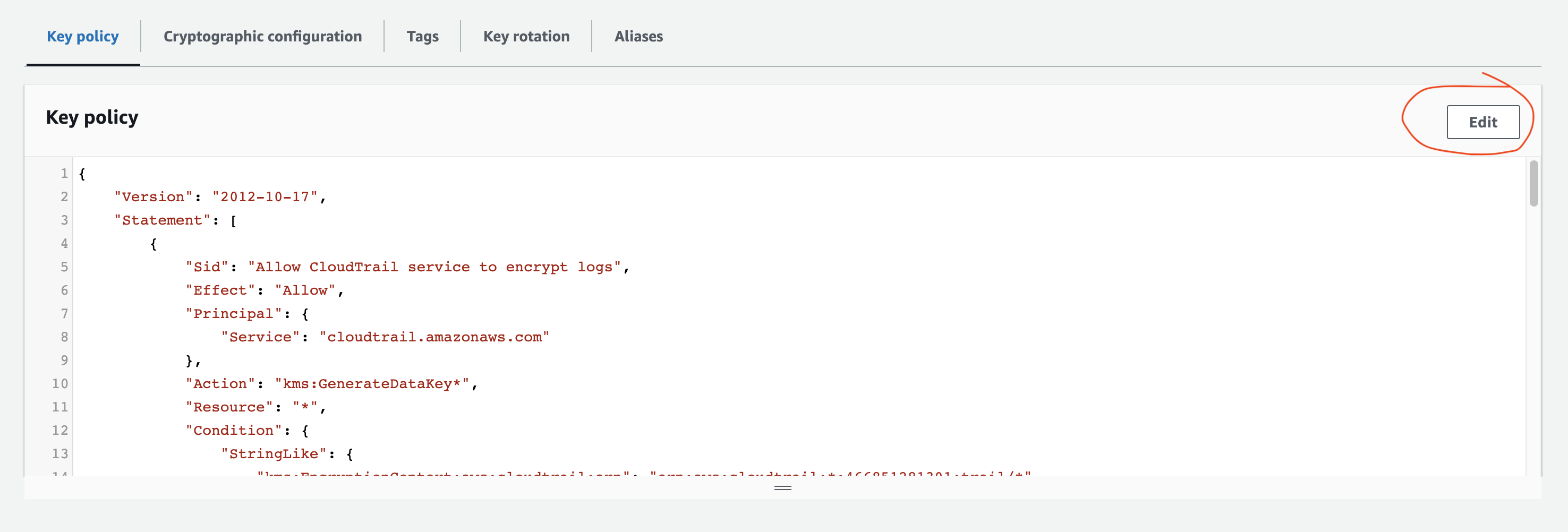
-
Add the necessary policy statement, replacing <HOME_REGION>, <MANAGEMENT_ACCOUNT_ID>, and <KMS_KEY_ID> with your account-specific values:
{
"Sid": "Allow Config to use KMS for encryption",
"Effect": "Allow",
"Principal": {
"Service": "config.amazonaws.com"
},
"Action": ["kms:Decrypt", "kms:GenerateDataKey"],
"Resource": "arn:aws:kms:<HOME_REGION>:<MANAGEMENT_ACCOUNT_ID>:key/<KMS_KEY_ID>"
} -
Add the following CloudTrail policy statement to the list of statements, replacing <HOME_REGION>, <MANAGEMENT_ACCOUNT_ID>, and <KMS_KEY_ID> with your account-specific values:
{
"Sid": "Allow CloudTrail to use KMS for encryption",
"Effect": "Allow",
"Principal": {
"Service": "cloudtrail.amazonaws.com"
},
"Action": ["kms:GenerateDataKey*", "kms:Decrypt"],
"Resource": "arn:aws:kms:<HOME_REGION>:<MANAGEMENT_ACCOUNT_ID>:key/<KMS_KEY_ID>",
"Condition": {
"StringEquals": {
"aws:SourceArn": "arn:aws:cloudtrail:<HOME_REGION>:<MANAGEMENT_ACCOUNT_ID>:trail/aws-controltower-BaselineCloudTrail"
},
"StringLike": {
"kms:EncryptionContext:aws:cloudtrail:arn": "arn:aws:cloudtrail:*:<MANAGEMENT_ACCOUNT_ID>:trail/*"
}
}
}
-
-
Click Save Changes.
-
Configure Control Tower
Setting up Control Tower for the first time can take over an hour, with most of the time spent waiting for operations to complete.
Start Control Tower setup
-
Sign in to the AWS Management Console using administrator credentials.
-
Navigate to the AWS Control Tower Console.
-
Verify that you are working in your desired home region.
cautionThe home region is where most workloads or data will reside. This region cannot be changed after setup. Refer to Administrative Tips for Landing Zone Setup for guidance.
-
Click Set up landing zone.
Review pricing and select regions
-
Under Region deny setting, select Enabled to ensure policies and controls cannot be bypassed using non-governed regions.
-
Under Select additional Regions for governance, choose all regions where operations will occur.
Details
Screenshot
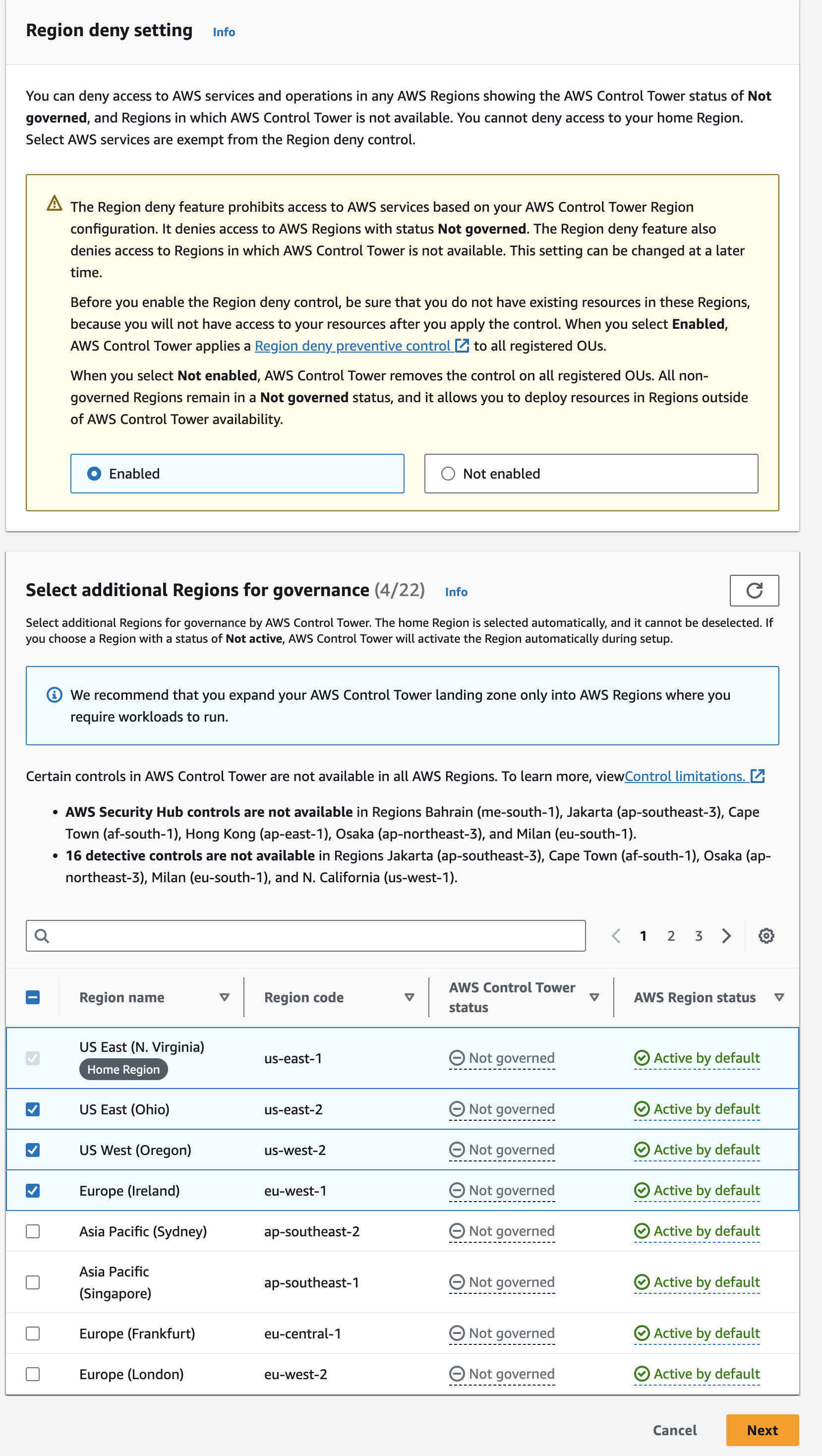
-
Click Next.
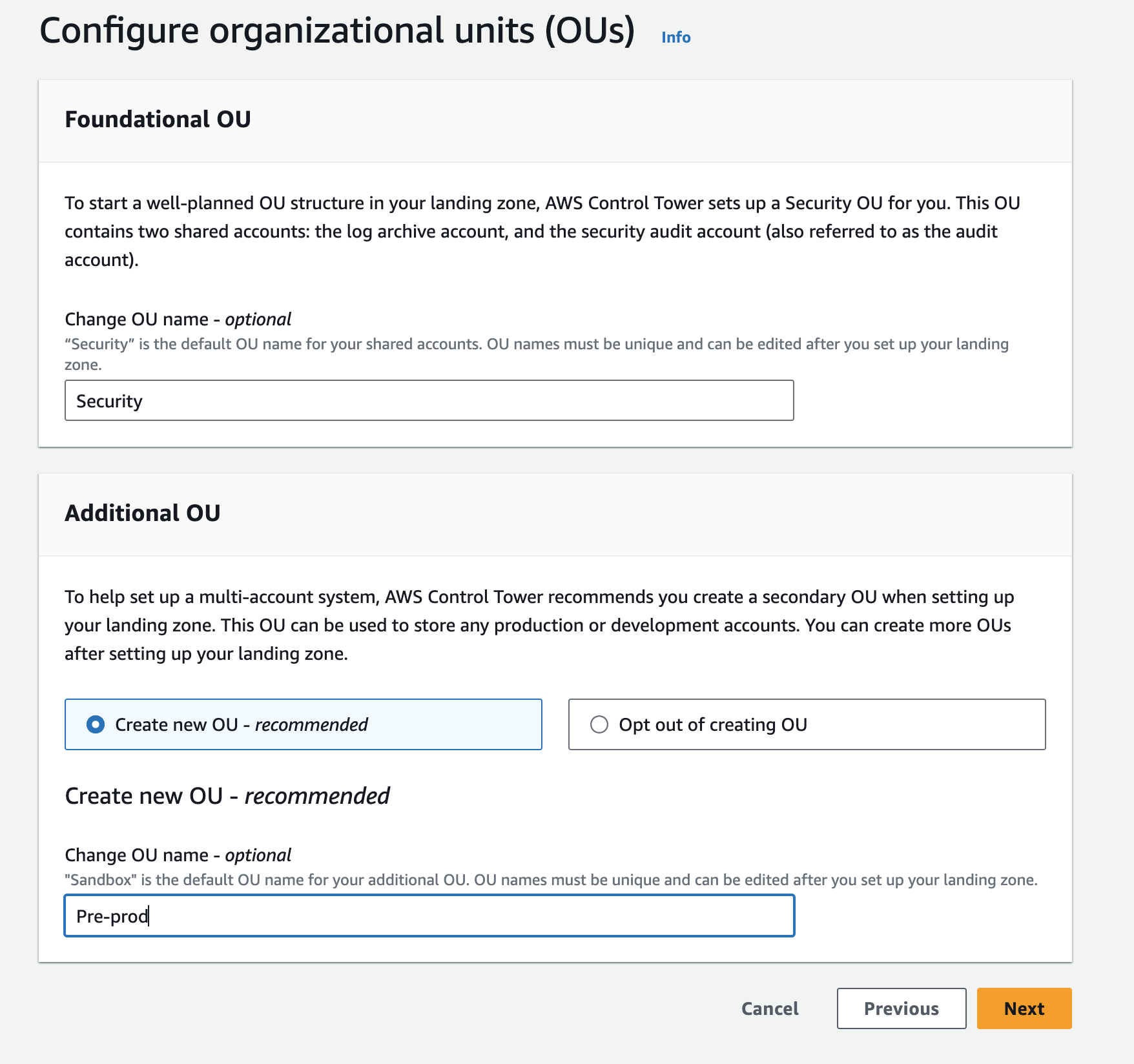
Configure Organizational Units (OUs)
-
Rename the "Additional OU" to "Pre-prod" (Note the casing of the name here).
Details
Screenshot
-
Click Next.
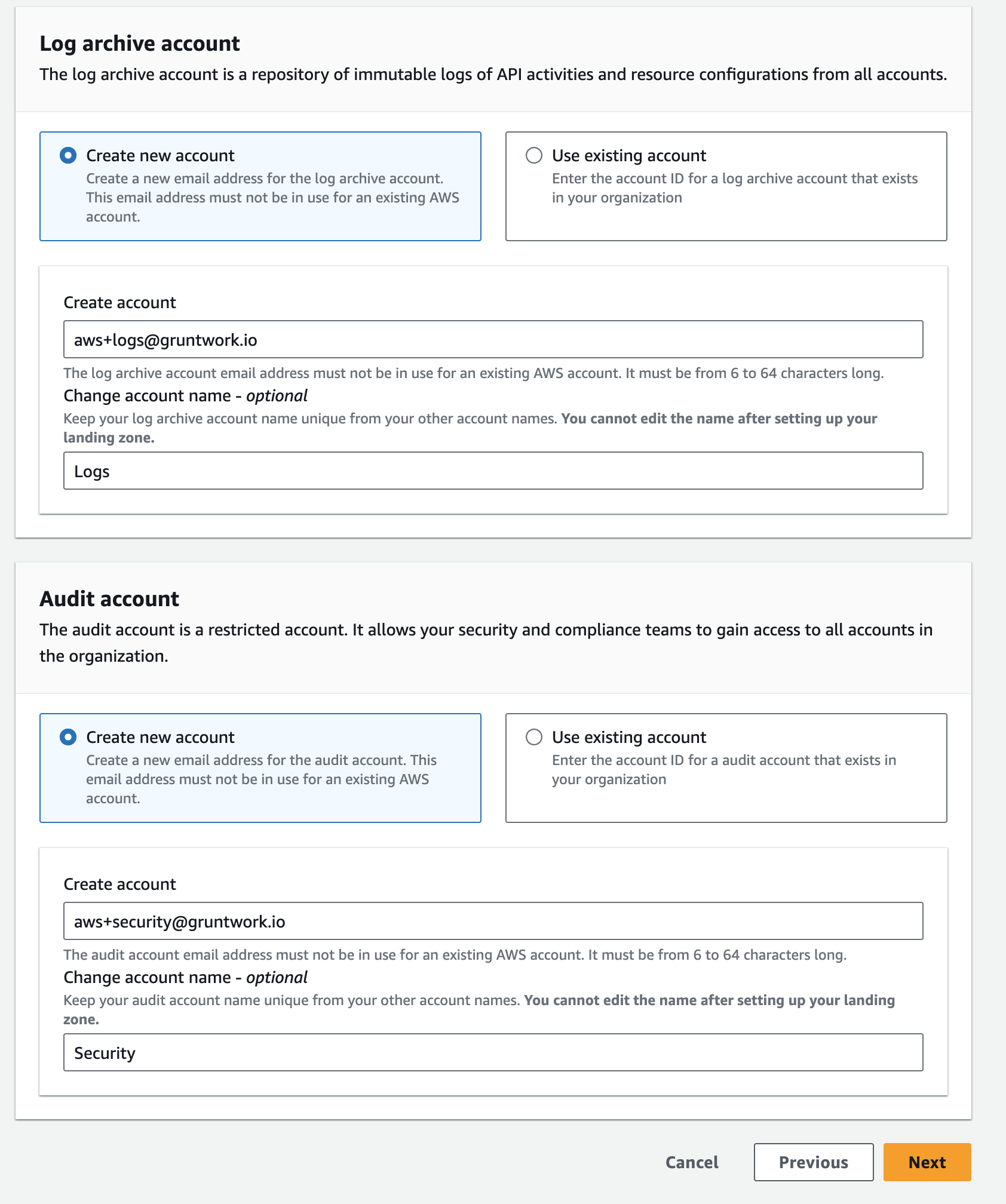
Configure shared accounts
-
Under Logs archive account, enter an email address and rename
Logs ArchivetoLogs. -
Under Audit account, enter an email address and rename
AudittoSecurity.cautionAccount names cannot be changed after setup. Ensure accuracy before proceeding.
Details
Screenshot
-
Click Next.
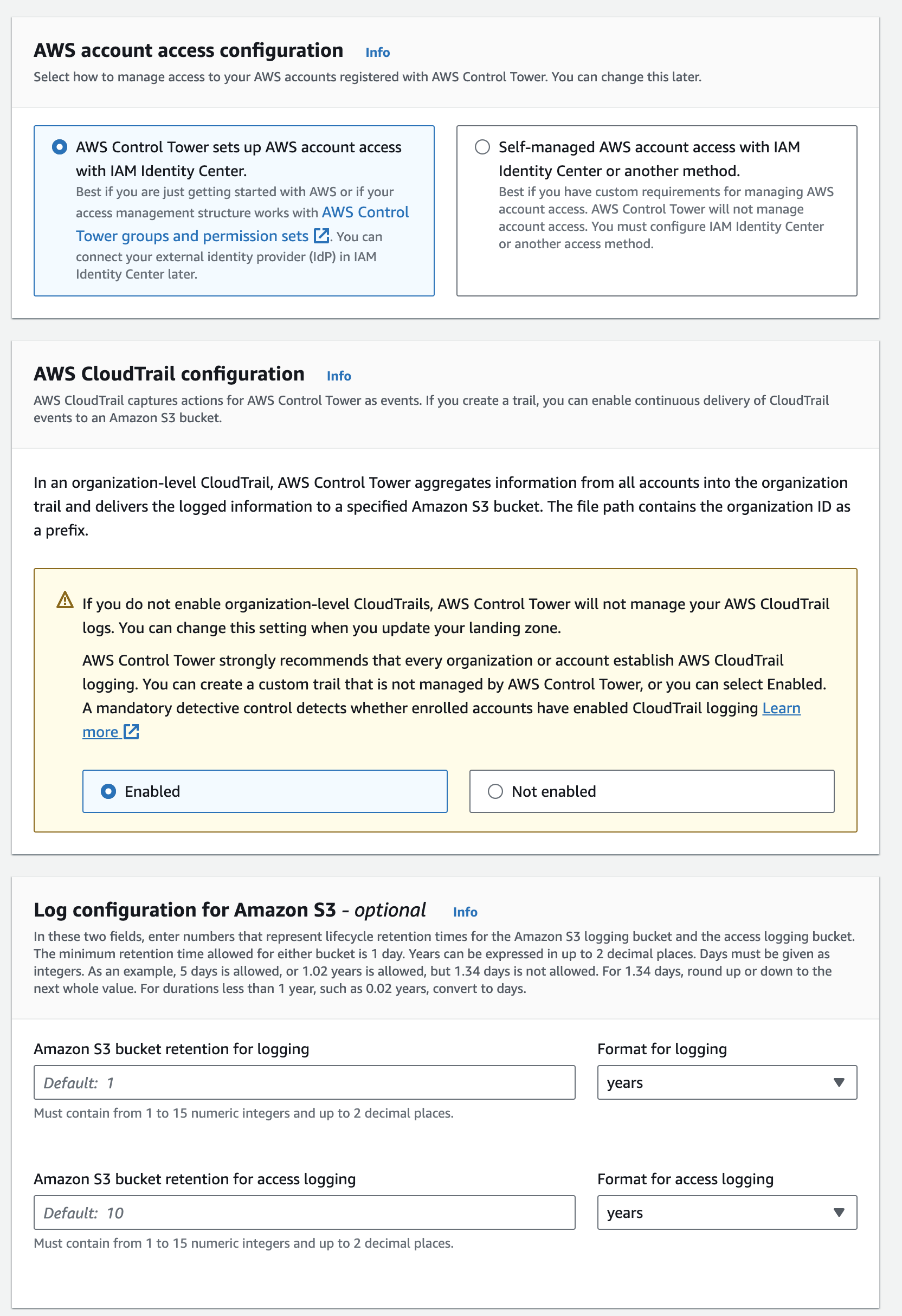
Additional configurations
-
Ensure settings match the defaults.
Details
Screenshot
-
Under KMS Encryption, check Enable and customize encryption settings.
-
Select the KMS Key created earlier.
-
Click Next.
Finish Control Tower setup
Control Tower creation will take approximately one hour.
-
Review settings, accept permissions, and click Set up landing zone.
-
You will see a notification with the estimated time for completion.
Details
Screenshot
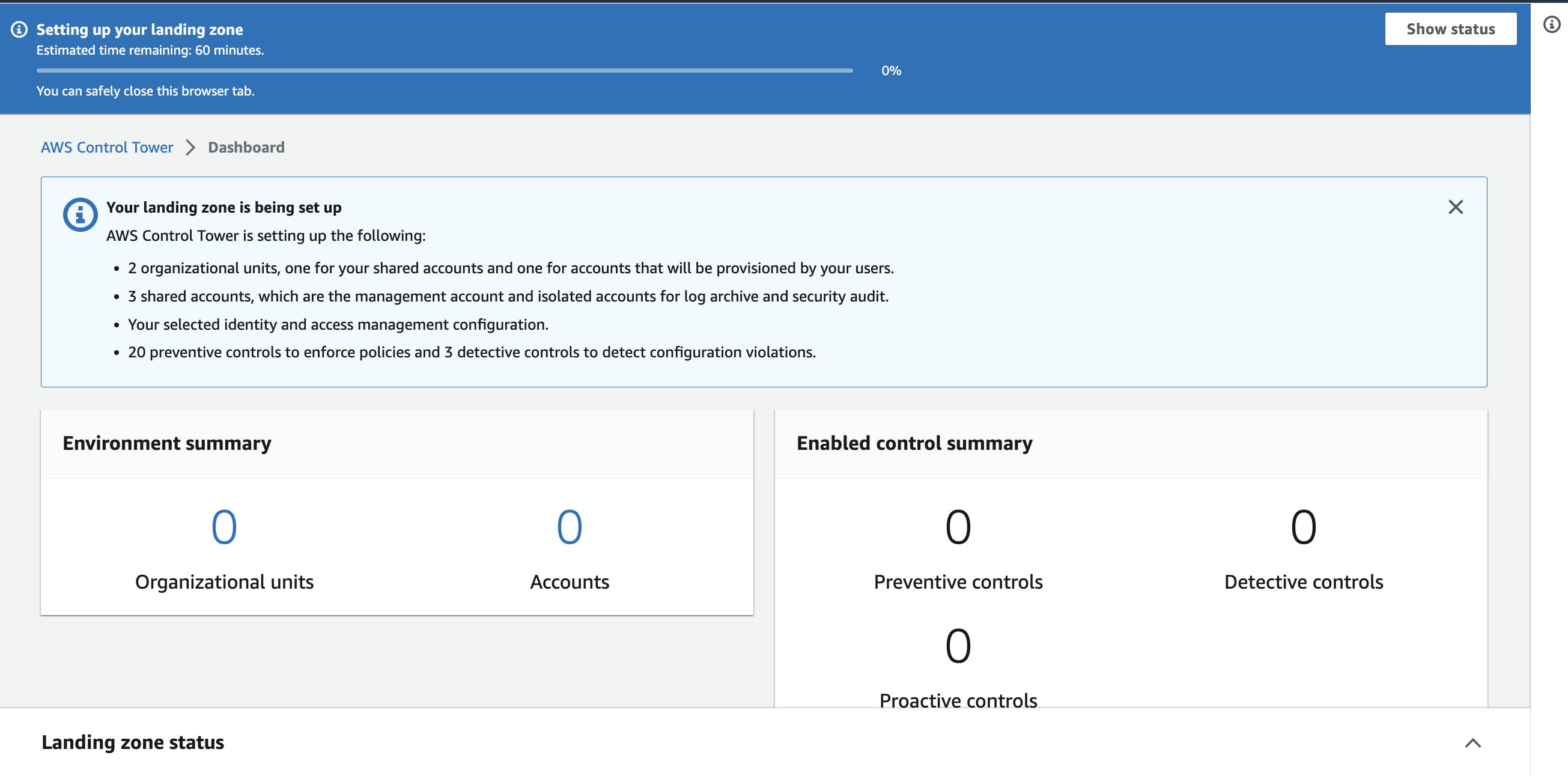 tip
tipYou can safely close your browser tab once you see this notice. The setup process will proceed unaffected in the background.
-
Invitations will be sent to the Root user (designed as the Control Tower Admin) for signing in using AWS IAM Identity Center. Once accepted, the Root user can access the Root, Logs, and Security accounts via the Identity Center Access Portal.
Details
Screenshot
Post-setup configuration
Complete the following steps to prepare for Gruntwork Account Factory:
- Disable the default VPC created for new accounts. Gruntwork Account Factory will create VPCs as needed.
- Create a shared account in a
ProdOU:-
Navigate to the AWS Control Tower Organization Dashboard.
-
Choose Create Resources >
Create organizational unit. -
Create a Prod OU with the Root OU as the parent.
-
Choose Create Resources >
Create account. -
Name the account
Shared, use the shared email address from the prerequisites, and assign it to theProdOU.tipThe shared account is intended for shared resources like KMS Keys, AMIs, or ECR repositories.
-
Assign IAM Identity Center user access to the
Sharedaccount.-
Navigate to IAM Identity Center, then click AWS accounts under Multi-account permissions in the side menu
-
Select the
Sharedaccount from theProdOU dropdown and click Assign users or groups -
Switch to the
Userstab, select your management user from the list and click Next -
Select
AWSAdministratorAccessfrom the list of Permission Sets, then click Next -
Click
Submitto finish assigning access to your user
-
-
Next steps
Now that Control Tower is configured, consider these next steps: