API Gateway Account Settings Module
This module allows you set the regional settings required to allow API Gateway to write to CloudWatch logs.
Overview
Each Region in AWS must be configured with an IAM Role that gives API Gateway permissions to create and write to CloudWatch logs. Without this configuration, API Gateway will not be able to write logs. This configuration is done regionally (only once per region) irrespective of the number of API Gateways deployed in that region.
This module creates an IAM role, assigns it the appropriate permissions and sets it as the "CloudWatch log role ARN" in the API Gateway configuration.
The corresponding screen from the AWS Console is shown below:
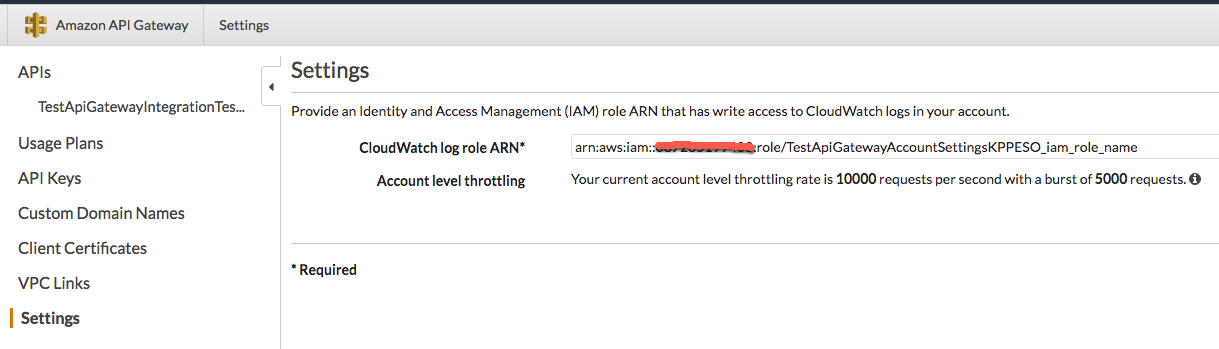 image
image
Quick start
Check out the examples for sample code that demonstrates how to use this module.
Sample Usage
- Terraform
- Terragrunt
# ------------------------------------------------------------------------------------------------------
# DEPLOY GRUNTWORK'S API-GATEWAY-ACCOUNT-SETTINGS MODULE
# ------------------------------------------------------------------------------------------------------
module "api_gateway_account_settings" {
source = "git::git@github.com:gruntwork-io/terraform-aws-lambda.git//modules/api-gateway-account-settings?ref=v1.3.0"
# ----------------------------------------------------------------------------------------------------
# OPTIONAL VARIABLES
# ----------------------------------------------------------------------------------------------------
# Set to false to have this module create no resources. This weird parameter
# exists solely because Terraform does not support conditional modules.
# Therefore, this is a hack to allow you to conditionally decide if the API
# Gateway account settings should be created or not.
create_resources = true
# The name of the IAM role that will be created to grant API Gateway rights to
# cloudwatch
iam_role_name = "api_gateway_cloudwatch_global"
# Time to wait after creating managed policy, to avoid eventual consistency
# races. Default: 60s.
managed_policy_waiting_time = "60s"
# When true, all IAM policies will be managed as dedicated policies rather
# than inline policies attached to the IAM roles. Dedicated managed policies
# are friendlier to automated policy checkers, which may scan a single
# resource for findings. As such, it is important to avoid inline policies
# when targeting compliance with various security standards.
use_managed_iam_policies = true
}
# ------------------------------------------------------------------------------------------------------
# DEPLOY GRUNTWORK'S API-GATEWAY-ACCOUNT-SETTINGS MODULE
# ------------------------------------------------------------------------------------------------------
terraform {
source = "git::git@github.com:gruntwork-io/terraform-aws-lambda.git//modules/api-gateway-account-settings?ref=v1.3.0"
}
inputs = {
# ----------------------------------------------------------------------------------------------------
# OPTIONAL VARIABLES
# ----------------------------------------------------------------------------------------------------
# Set to false to have this module create no resources. This weird parameter
# exists solely because Terraform does not support conditional modules.
# Therefore, this is a hack to allow you to conditionally decide if the API
# Gateway account settings should be created or not.
create_resources = true
# The name of the IAM role that will be created to grant API Gateway rights to
# cloudwatch
iam_role_name = "api_gateway_cloudwatch_global"
# Time to wait after creating managed policy, to avoid eventual consistency
# races. Default: 60s.
managed_policy_waiting_time = "60s"
# When true, all IAM policies will be managed as dedicated policies rather
# than inline policies attached to the IAM roles. Dedicated managed policies
# are friendlier to automated policy checkers, which may scan a single
# resource for findings. As such, it is important to avoid inline policies
# when targeting compliance with various security standards.
use_managed_iam_policies = true
}
Reference
- Inputs
- Outputs
Optional
create_resourcesboolSet to false to have this module create no resources. This weird parameter exists solely because Terraform does not support conditional modules. Therefore, this is a hack to allow you to conditionally decide if the API Gateway account settings should be created or not.
trueiam_role_namestringThe name of the IAM role that will be created to grant API Gateway rights to cloudwatch
"api_gateway_cloudwatch_global"Time to wait after creating managed policy, to avoid eventual consistency races. Default: 60s.
"60s"When true, all IAM policies will be managed as dedicated policies rather than inline policies attached to the IAM roles. Dedicated managed policies are friendlier to automated policy checkers, which may scan a single resource for findings. As such, it is important to avoid inline policies when targeting compliance with various security standards.
true